
Click with Caution

When was the last time you received a suspicious email, call, or message? What did you do?
These urgent or unexpected messages often come from cybercriminals. They use social engineering tactics to manipulate our behaviors and emotions. Their goal is to get us to share sensitive information.
Read more below to recognize, relax, and rethink what to do when you receive a suspicious message.
Want to take the safest route? Be safe, not sorry and report suspicious emails to the Information Security Office (ISO), right away!
What is phishing?
Phishing messages masquerade as legitimate communications to trick us into revealing sensitive information. This often includes our usernames, passwords, credit card numbers, and other personal data.
While phishing frequently refers to emails, it doesn't end there. Phishing can also happen via text messages and voice calls. These can lead you to fake websites including fake login screens.

Be mindful to be cyber safe
RECOGNIZE
Cybercriminals use email, text, and phone calls to try and fool us. Be alert and know what to look for.
RELAX
Take a moment to be mindful and pause before reacting to unexpected or suspicious messages.
RETHINK
Consider the best way to react – think about going to the source, reporting, or asking for help.
"Recognize"

Think outside the inbox
There’s more to phishing than just email. Be in the know with some new terminology to help you steer clear of cybercriminals.
Have you ever received a suspicious phone call? You may have been the target of voice call phishing, also known as vishing. It’s always best to be wary of unsolicited calls requesting personal information.
Suspicious messages even extend to text messaging! Phishing that takes place over a text or SMS message is called smishing. Be alert for bad actors posing as someone we know or recently met.
FUDGE model of common phishing tactics
We receive A LOT of emails, phone calls, and text messages. Know when to tell the real stuff from the fake stuff using our FUDGE model. Phishing messages often show one or more of the following signs.
 |
Fear |
The message is trying to scare you into giving information or taking an action. |
 |
Urgency |
The message is saying you must take immediate action, “or else”. |
 |
Desire
|
The message appears to come from someone you want to please, like a boss or executive. It makes you feel like you are doing the “right” thing, even though it doesn’t seem normal. |
 |
Greed |
The message is saying you are the winner of something you want. If it seems too good to be true, it probably is. |
 |
Emotion |
The message is playing at your emotions. Trust your gut. If you feel something is off, don’t take action, click the link, or open the attachment. |
"Relax"
Pause before responding
Cybercriminals know we're more likely to fall for a scam when we're busy or urged into quick action. That's why it's so important to pause and be mindful before responding to messages.
Pausing to consider the validity of a request helps us avoid falling for scams. Pausing also helps prevent quick responses that might be against our better judgment.

Be aware of where you're browsing
Have you ever visited a website that felt suspicious? Bad actors also try to fool us using fraudulent websites. They want to trick us into providing sensitive data like our login credentials and financial information.
Malicious websites are often designed to appear exactly like legitimate sites. This can make it difficult to tell if a website is real or fake.
Use these tips to outsmart the internet and help make sure you're browsing safely.
- Always check the website URL - only browse sites that use official addresses.
- Go straight to the source - don't click unexpected links received in emails or other messages.
- Look for the “https” in the URL - if you only see “http” the site is not secure.
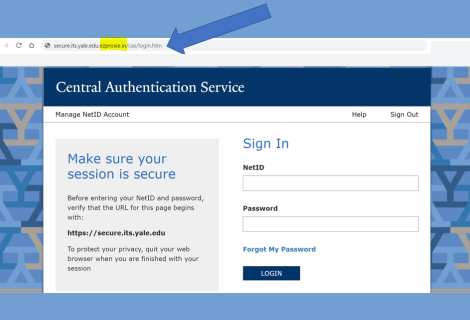
Common Yale URLs
Avoid browsing sites that use unfamiliar or misspelled URLs. For example, the screenshot seen here shows a fraudulent URL for the CAS login page.
Be sure to familiarize yourself with the official URLs used for Yale websites and services. Here's a few commonly-used Yale URLs you should recognize.
CAS Login
https://secure.its.yale.edu
Microsoft Online Login
https://login.microsoftonline.com/
"Rethink"
Sometimes responding isn't the best answer
We should also consider how we react when responding to requests. Most often it's the communication methods we know and trust that cybercriminals target. They'll even impersonate people we know!
Ask yourself these questions before reacting to an unusual request:
- Am I sure this request is coming from the person I think it is?
- Is this request unusual, suspicious, or outside the norm?
- Would I rather:
- Confirm with the source?
- Or take a chance and risk losing access to my work and exposing Yale data or resources?
Don't get lured by phishing
Phishing messages are improving all the time making it hard to tell an authentic message from a fake. Follow these guidelines to stay ahead of bad actors.
DON’T
- Click on links in unexpected or suspicious messages.
- Open unsolicited email attachments.
- Share your username or password or enter credentials on an unfamiliar website.
DO
- Verify the legitimacy of a request before providing sensitive information.
- Go straight to the source when in doubt.
- Trust your gut if something seems suspicious.
- Report suspicious or fraudulent emails.
- Only approve MFA requests when you are actively logging in to a Yale service.
Additional resources to build your cyber muscles!
- Download our Click with Caution infographic.
- Test your knowledge with Google's phishing quiz.
- Sign up for cybersecurity awareness alerts and subscribe to our Bee Cyber Fit monthly tip, newsletter, and podcast.
- Request cybersecurity awareness training, presentations, and activities for your team or department.

Report suspicious cyber activity, right away - including suspicious emails!
Feeling hesitant, embarrassed, or unsure? Even if it winds up being nothing, it's better to be safe not sorry. Go with your gut if something seems unusual or suspicious.
You can also check out our Bee SAFE, Not Sorry model for recognizing, reporting, and responding to cybersecurity incidents.